Bandit is a beginner-level wargame hosted by OverTheWire, which is designed to help users learn and practice the basic concepts of Linux command-line and security.
The game consists of a series of levels, each containing a different set of challenges that require the player to use their knowledge of Linux commands and system vulnerabilities to find passwords hidden in files or to gain access to restricted areas.
As the player progresses through the levels, the challenges become increasingly difficult, requiring more advanced techniques and deeper understanding of security concepts.
You can find more information about it click :
Level 00
Level goal
To progress to Level 1, you must successfully log in to the game through SSH. More about SSH here : SSH
Level solution
Simple enough isn’t it ?
- username : bandit0
- password : bandit0
All that’s left is to connect, using port 2220
1
ssh bandit0@bandit.labs.overthewire.org -p 2220
Level 00 –> 01
Level credentials
- username : bandit0
- password : bandit0
Level goal
To progress to the next level, locate the password within the readme file in the home directory. Use this password to log in to bandit1 via SSH. After discovering the password for a level, always use SSH on port 2220 to access that level and proceed with the game.
Level solution
Well, reading the instructions, what we need to do is :
- list all of the files in our current directory
1
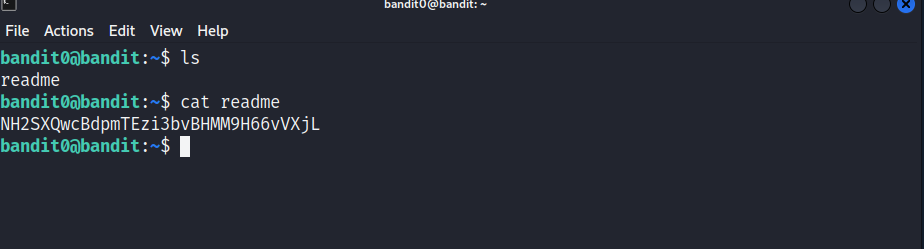
ls
- locate a file named readme and display its content
1
cat readme
We got our password 😃
NH2SXQwcBdpmTEzi3bvBHMM9H66vVXjL
Level 01 –> 02
Level credentials
- username : bandit1
- password : NH2SXQwcBdpmTEzi3bvBHMM9H66vVXjL
Level goal
The password for the next level is stored in a file called - located in the home directory
Level solution
This level is a bit tricky, if you trie cat - , it won’t work,that’s because - represents the standard input, e.g cat will read the input from your keyboard, and display it to the standard output. To read the actual file, we need to provide its path.
1
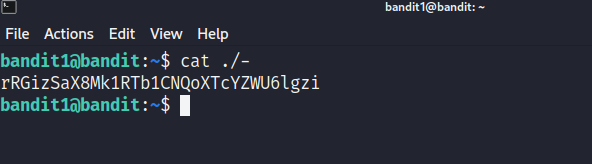
cat ./-
We got our password 😃
rRGizSaX8Mk1RTb1CNQoXTcYZWU6lgzi
Level 02 –> 03
Level credentials
- username : bandit2
- password : rRGizSaX8Mk1RTb1CNQoXTcYZWU6lgzi
Level goal
The password for the next level is stored in a file called spaces in this filename located in the home directory
Level solution
This level is kind of free, here is a simple methode to solve it:
- Type
catfollowed by s, then hittabin your keyboard.You can also type the full name using quotes
1
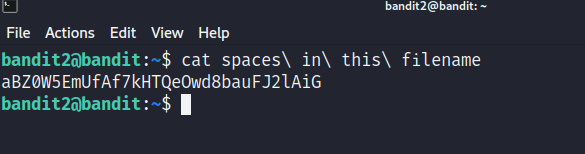
cat spaces\ in\ this\ filename
We got our password 😃
aBZ0W5EmUfAf7kHTQeOwd8bauFJ2lAiG
Level 03 –> 04
Level credentials
- username : bandit3
- password : aBZ0W5EmUfAf7kHTQeOwd8bauFJ2lAiG
Level goal
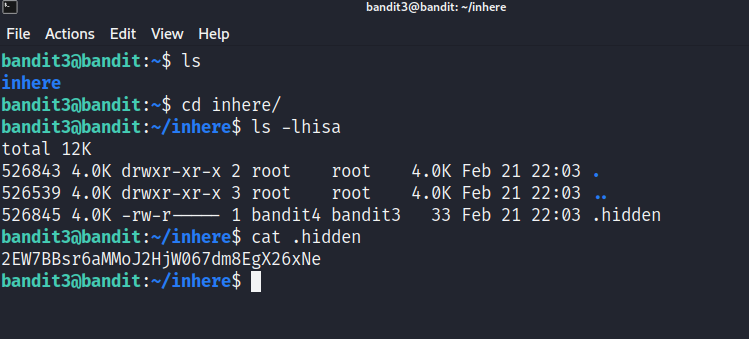
The password for the next level is stored in a hidden file in the inhere directory.
Level solution
The solution is straightforward :
- change directory to
inhere
1
cd inhere
- list all of the files , including the hidden ones
1
ls -lhisa
catthe content of the hidden file
1
cat .hidden
We got our password 😃
2EW7BBsr6aMMoJ2HjW067dm8EgX26xNe
Level 04 –> 05
Level credentials
- username : bandit4
- password : 2EW7BBsr6aMMoJ2HjW067dm8EgX26xNe
Level goal
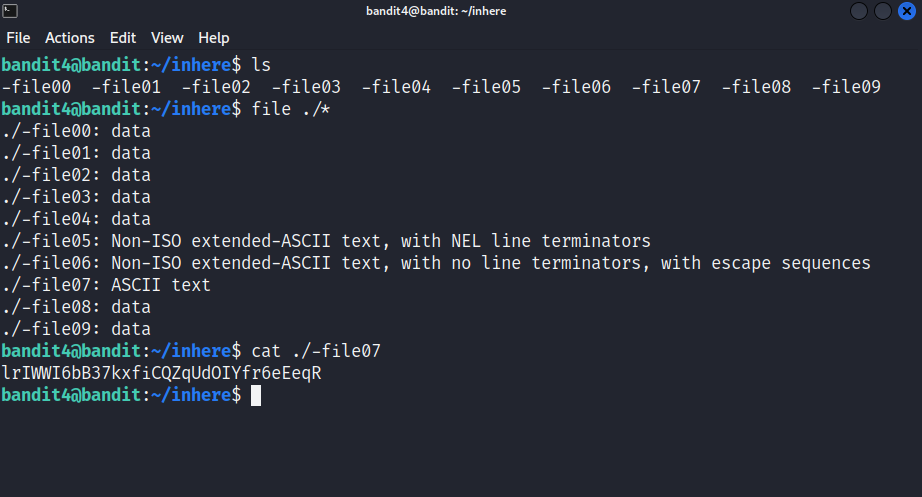
The password for the next level is stored in the only human-readable file in the inhere directory.
Level solution
Ok, let’s visite the inhere directory.
1
cd inhere
Listing the directory’s content, we notice 10 files, all starting with - in their name. We know that our password is stored in a unique human-readable file, we can leverage that by determining the file type of all the files. To determine the type of a file, we can use file <file_name> To determine the type of all files in a directory , we can use the wildcard * . But remember, all the files start with a hyphon, we need to provide the path of the files as we saw in the previous levels.
1
file ./*
Doing so, we can clearly see that the only distinguishable file is -file07.
1
cat ./-file07
We got our password 😃
lrIWWI6bB37kxfiCQZqUdOIYfr6eEeqR